
Validating the security of your MikroTik routers network-wide
Using Unimus to check if your RouterOS devices are compromised across your whole network. Also a look at how to audit and fix security holes for old and new MikroTik exploits alike.
Introduction
Recently, there has been a resurgence of attacks on MikroTik RouterOS devices (articles here, here and here) using vulnerabilities that were fixed in April 2018 (release 6.42.1), but also falling back to some older vulnerabilities.
These new attacks primarily use an exploit in Winbox (one of MikroTiks management interfaces), to gain control of the router, and perform various malicious tasks. These Winbox exploit are far from the only exploits that exist for RouterOS however. For example, the http(s) server in older versions of RouterOS contains an exploit that was made public during the Vault7 leaks.
In this article, we will use Unimus to check if any of your routers are compromised across your whole network. We will also look into how to use Unimus to both audit and fix potential security holes for old and new MikroTik exploits alike.
Preparations
For this article, we will assume you have the devices you want to audit / secure already in Unimus, and they are properly discovered. If this is not the case, we suggest checking out our Wiki, and/or video tutorials.
We will be creating various Mass Config Push presets, but if you wish you can run all of these steps in sequence inside a single Mass Config Push. Using multiple presets just makes it easier and more organized to audit your network.
Each of the following sections contains a single security check / fix. When you run these commands, you might see multiple Mass Config Push output groups. We recommend checking each group for corresponding output.
For example, when running the "Checking if routers are exploited" preset, you might see 2 output groups. One output group will contain 45 devices, and the other 2 devices. In this example, when you inspect both output groups, you should find that 45 devices are exploit-free, and the other 2 have been infected.
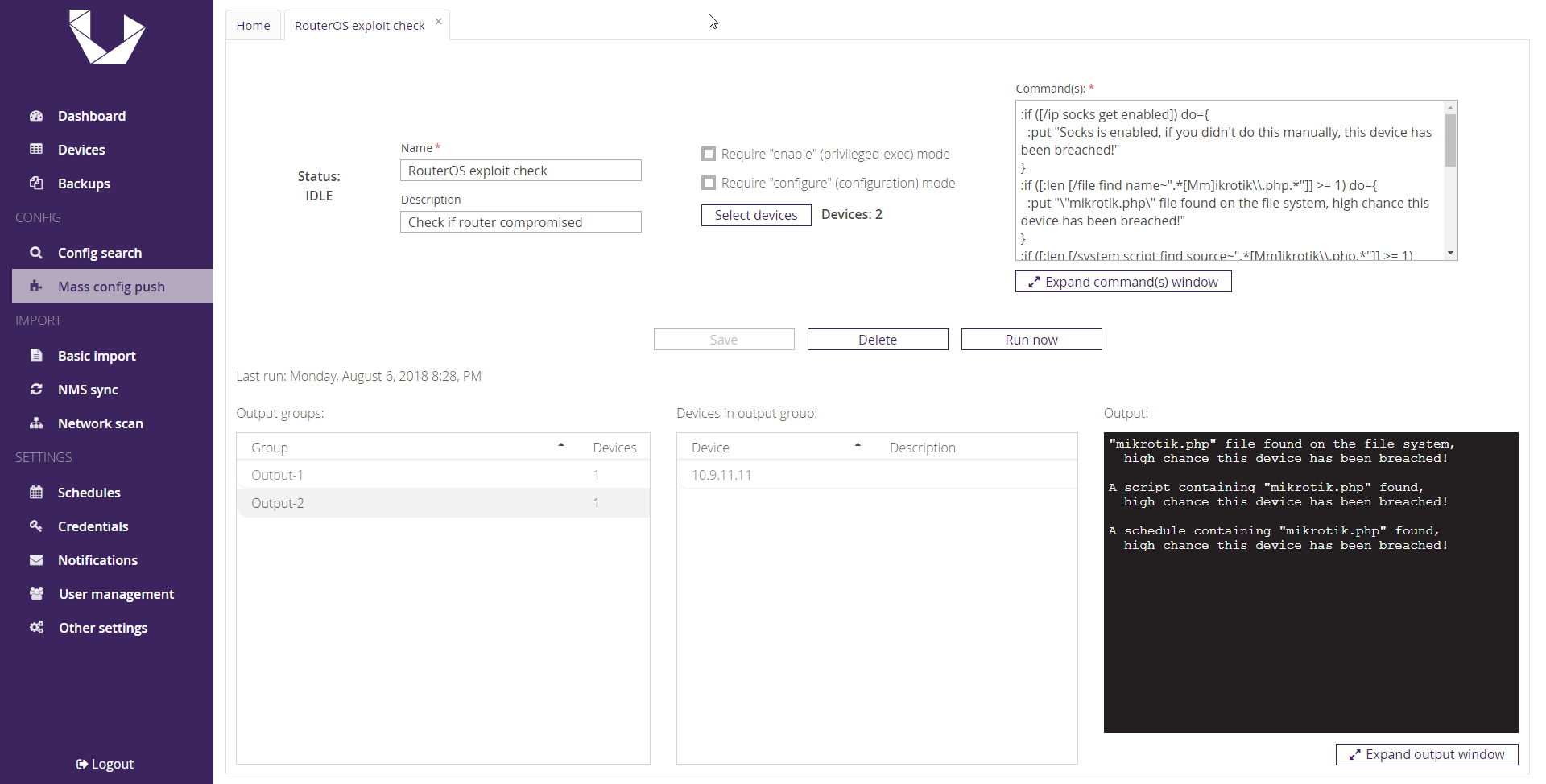
Checking if routers are exploited
This preset will check if any of your devices have been exploited using any of the latest RouterOS exploits.
:if ([/ip socks get enabled]) do={
:put "Socks is enabled, if you didn't do this manually, this device has been breached!"
}
:if ([:len [/file find name~".*[Mm]ikrotik\\.php.*"]] >= 1) do={
:put "\"mikrotik.php\" file found on the file system, high chance this device has been breached!"
}
:if ([:len [/system script find source~".*[Mm]ikrotik\\.php.*"]] >= 1) do={
:put "A script containing \"mikrotik.php\" found, high chance this device has been breached!"
}
:if ([:len [/system scheduler find on-event~".*[Mm]ikrotik\\.php.*"]] >= 1) do={
:put "A scheduled script containing \"mikrotik.php\" found, high chance this device has been breached!"
}
:if ([:len [/user find name~".*service.*"]] >= 1) do={
:put "\"service\" user exists, if you didn't create this user manually, this device has been breached!"
}If no devices in your network have been breached, you will see only a single output group, with empty output. If you see any other output groups, devices in those output groups have been compromised. The content of the output group will tell you which of the exploit checks matched on those devices.
How to remediate if a device has been exploited
Simply create a Mass Config Push preset like this:
/ip socks
set enabled=no
set port=1080
/file
:foreach i in=[find name~".*[Mm]ikrotik\\.php.*"] do={
remove $i
}
/system script
:foreach i in=[find source~".*[Mm]ikrotik\\.php.*"] do={
remove $i
}
/system scheduler
:foreach i in=[find on-event~".*[Mm]ikrotik\\.php.*"] do={
remove $i
}
/user
:foreach i in=[find name~".*service.*"] do={
remove $i
}Run this on the affected devices.
Make sure to change the password (preferably also username) you use to access the affected devices AFTER you remediate the exploits.
Checking if your routers have firewall
Having a properly firewalled input chain on your MikroTiks is super important. This preset checks if your firewall exists, and has an explicit drop rule in the input chain.
/ip firewall filter
:if ([:len [find]] = 0) do={
:put "No firewall configured on this device"
} else={
:if ([:len [find chain=input]] = 0) do={
:put "No input firewall configured on this device"
} else={
:if ([:len [find chain=input action=drop !connection-state]] = 0) do={
:put "No explicit drop rule in input firewall configured on this device"
}
}
}How to remediate
There is sadly no simple response to this one. You will have to build a proper firewall for your needs. (if there is enough interest, we might write a separate article on this one)
Checking service ACLs (address restrictions)
If for some reason you do not want to have firewall on your routers (this should never be the case - you can use "/ip firewall raw" if you want to fasttrack some traffic), you must secure the services on RouterOS to only certain IPs (or IP ranges).
If you DO have firewall properly configured, it will already protect these services, so with a proper firewall setup, limiting access to services is not essential. You can however use this as a 2nd line of defence.
/ip service
:foreach i in=[find] do={
:if ((![get $i disabled]) && ([get $i address] = "")) do={
:put ([get $i name] . " service is not restricted to any address!")
}
}How to remediate
You can push the following change to your devices:
{
:local address "1.2.3.4"
/ip service
:foreach i in=[find] do={
set $i address=$address
}
}Make sure to properly change the address variable in the 1st line.
Update RouterOS to latest the version
All of the exploits currently running wild use vulnerabilities that have been fixed in the latest RouterOS versions. Even after improving security using the above methods, it is highly recommended to upgrade to the latest RouterOS release.
We have a separate blog article on how to update RouterOS to the latest version across your entire network here: https://blog.unimus.net/network-wide-mikrotik-routeros-upgrade-with-unimus/
Final words
That's it for this blog article, we hope it will help you at least a little with your network security. If you are new to Unimus, check out our website to learn more about us!
We are offering an unlimited trial license if you want to give Unimus a try (independently of our free tier)! Click here to learn more!
