Unimus Security
Unimus is built with a strong focus on security. The platform can be deployed fully on-premises, ensuring that no configuration data ever leaves your network. All data is encrypted in transit and at rest, user access is tightly controlled with RBAC and MFA, and every component runs entirely under your ownership and control.
Architecture
Fully On-Premises
The Unimus server and database are hosted within your own network. No configuration data leaves your infrastructure.
The Unimus server and database are hosted within your own network. No configuration data leaves your infrastructure.
Air-Gapped Capable
Unimus supports fully isolated deployments with no external network access required.
Unimus supports fully isolated deployments with no external network access required.
Agentless Design
Unimus does not require installation of any agents on your network devices.
Unimus does not require installation of any agents on your network devices.
Highly Available
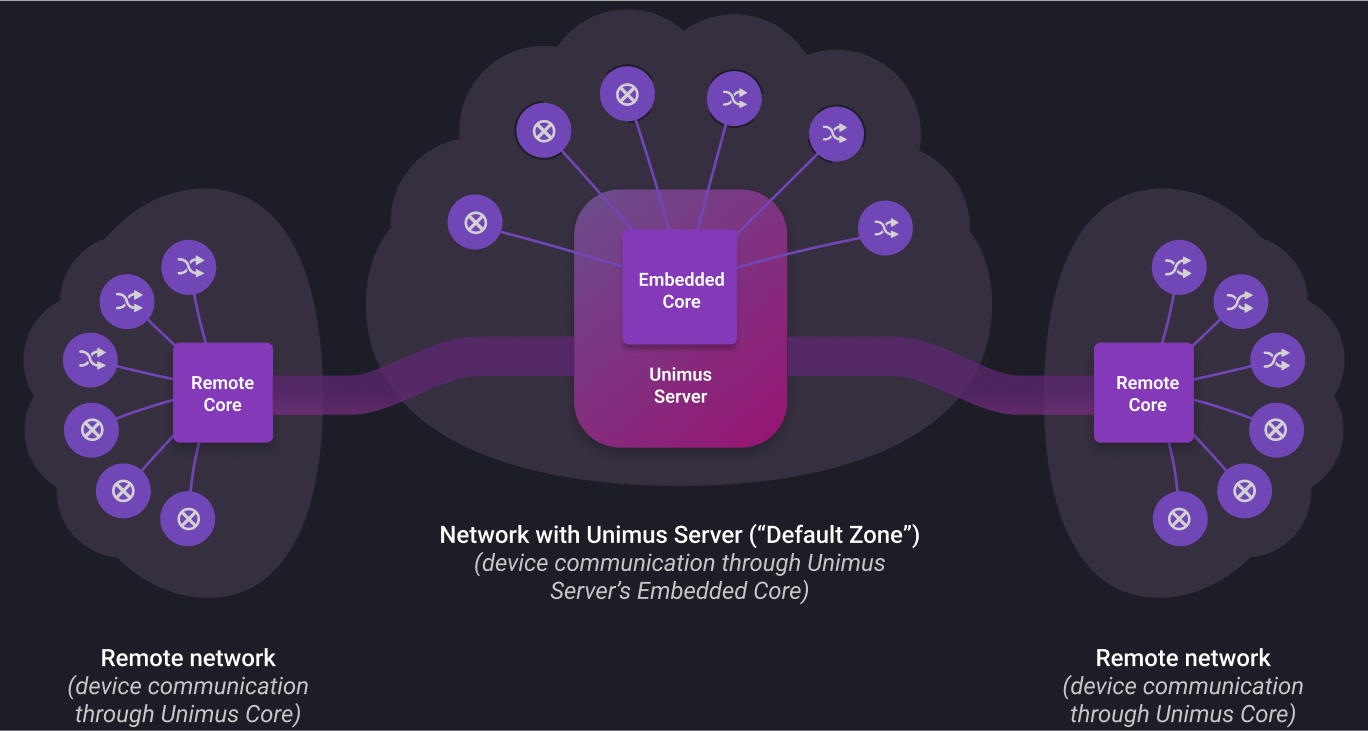
Unimus offers flexible deployment options tailored to your organizational needs, including distributed polling with high-availability support for the server and pollers (Remote Cores).
Unimus offers flexible deployment options tailored to your organizational needs, including distributed polling with high-availability support for the server and pollers (Remote Cores).
Data at Rest
Credential Encryption
All device credentials, API tokens, etc. are encrypted using a user-defined key with AES-128-CBC and PKCS5.
All device credentials, API tokens, etc. are encrypted using a user-defined key with AES-128-CBC and PKCS5.
Application-Layer Encryption
In addition to credential encryption, all sensitive data in the database are encrypted at the application layer before storage.
In addition to credential encryption, all sensitive data in the database are encrypted at the application layer before storage.
Your Data, Your Database
The Unimus database is fully under your control. Backup, storage, and access policies are governed by your organization.
The Unimus database is fully under your control. Backup, storage, and access policies are governed by your organization.
Data in Transit
Device Interaction
Unimus connects to your network devices via SSH, ensuring that every management session is both authenticated and encrypted.
Unimus connects to your network devices via SSH, ensuring that every management session is both authenticated and encrypted.
Core-to-Server Communication
Pollers (Remote Cores) establish a TCP session with the Unimus server, secured with AES-256 encryption and protected by a Pre-Shared Key (PSK).
Pollers (Remote Cores) establish a TCP session with the Unimus server, secured with AES-256 encryption and protected by a Pre-Shared Key (PSK).
Licensing Server Communication
The only outbound connection Unimus initiates is for licensing validation, using a standard HTTPS (TLS) request over TCP port 443.
The only outbound connection Unimus initiates is for licensing validation, using a standard HTTPS (TLS) request over TCP port 443.
Certifications & Penetration Testing
Security Certifications
Unimus is covered under ISO 9001:2015, ISO 22301:2019, ISO/IEC 27001:2022, and PCI DSS Merchant Compliance.
Unimus is covered under ISO 9001:2015, ISO 22301:2019, ISO/IEC 27001:2022, and PCI DSS Merchant Compliance.
Penetration Testing
Third‑party specialists conduct penetration tests on the Unimus Web GUI and API to identify and remediate vulnerabilities.
Third‑party specialists conduct penetration tests on the Unimus Web GUI and API to identify and remediate vulnerabilities.
Summary reports are available at https://security.netcore.software
Access Management
Role-Based Access Control
Built-in permission system allowing detailed user role definitions.
Built-in permission system allowing detailed user role definitions.
Object Access Policies
Granular access controls to your network devices in Unimus.
Granular access controls to your network devices in Unimus.
SSO and AAA support
SSO, LDAP and RADIUS support for easy access management.
SSO, LDAP and RADIUS support for easy access management.
Multi-Factor Authentication
Additional layer of security to prevent unauthorized account access.
Additional layer of security to prevent unauthorized account access.
System Access History
Accounting records with authentication context and time tracking.
Accounting records with authentication context and time tracking.
